Get A+ rating on Apache by ssllabs.com with a free cert from StartSSL
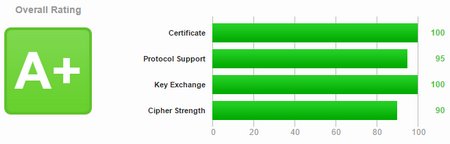
It is very easy to get an A+ rating at https://www.ssllabs.com with Apache for your website by using a free SSL certificate from https://www.startssl.com/ if you correctly generate the servers private key and add some simple configurations to your ssl.conf file. I tested this on Apache/2.2.15 running on CentOS 6.6.
Generate public/private key
First of all generate a private key with 4096 bits for your server. Let’s call it server2015.key
openssl genrsa -out server2015.key 4096
Generate the certificate signing request for a sha512bit certificate (CSR)
openssl req -sha512 -new -key server2015.key -out server2015.csr
Give CSR to startssl and receive certificate(s)
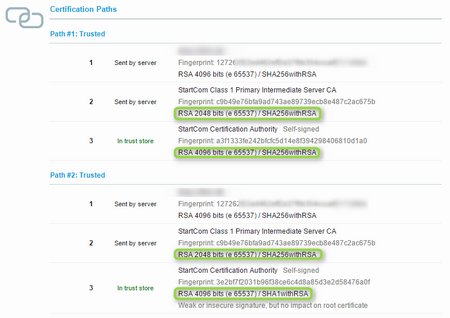
You will receive your certificate from startssl (let’s assume it is named server2015.crt. Please make sure you also download the sub.class1.server.ca.pem intermediate certificate from startssl. Don’t use their bundle (ca-bundle.pem), it contains some certificates with „weak“ algrorithms!
Place the certicates in the correct folders
server2015.crt –> /etc/pki/tls/certs/
sub.class1.server.ca.pem –> /etc/pki/tls/certs
server2015.key –> /etc/pki/tls/private <— DIFFERENT FOLDER !!!
Generate symbolic links
I recommend using symbolic links for the certificates so you can easily change them (next year) just by changing the symbolic links and reloading Apache.
cd /etc/pki/tls/certs
ln -s sub.class1.server.ca.pem current-ca-chain.pem
ln -s server2015.crt current.crt
Configure the use of the certificates in /etc/httpd/conf.d/ssl.conf
The following configuration paramters in ssl.conf will use the above certificates (symbolic links)
SSLCertificateFile /etc/pki/tls/certs/current.crt
SSLCertificateChainFile /etc/pki/tls/certs/current-ca-chain.pem
SSLCertificateKeyFile /etc/pki/tls/private/current.key
Change cipher suites (remove weak ciphers) from ssl.conf
Set the following in ssl.conf to only use strong ciphers
SSLProtocol all -SSLv2 -SSLv3
SSLHonorCipherOrder on
SSLCipherSuite ALL:!RC4:!MD5:!ADH:!EXP:!SSLv2:!LOW:!IDEA:RSA:+HIGH:+MEDIUM
Hint:
If you want to know which ciphers are used with the above configuration, just enter the string from „SSLCIpherSuite“ into openssl for an output of all ciphers:
openssl ciphers -v ‚ALL:!RC4:!MD5:!ADH:!EXP:!SSLv2:!LOW:!IDEA:RSA:+HIGH:+MEDIUM‘
With this configuration you should already get an „A“ at https://www.ssllabs.com
Enable HSTS for A+
If you enable HSTS on your site, a client (browser) that visited your site once via https will automatically switch to https even if it tries to connect via http. (works with Firefox and Chrome but not IE). This is needed to get an „A+“ rating!
Place the following lines in ssl.conf inside the <VirtualHost>…</VirtualHost> directive
The max-age is in seconds. In the example below it is 340days
#/etc/httpd/conf.d/ssl.conf
# enable HSTS (client will automatically choose https in the future if once connected via https
<IfModule headers_module>
Header always set Strict-Transport-Security „max-age=29376000“
</IfModule>
Sample ssl.conf (without comments)
LoadModule ssl_module modules/mod_ssl.so
Listen 443
SSLPassPhraseDialog builtin
SSLSessionCache shmcb:/var/cache/mod_ssl/scache(512000)
SSLSessionCacheTimeout 300
SSLMutex default
SSLRandomSeed startup file:/dev/urandom 256
SSLRandomSeed connect builtin
SSLCryptoDevice builtin
<VirtualHost _default_:443>
ErrorLog logs/ssl_error_log
TransferLog logs/ssl_access_log
LogLevel warn
SSLEngine on
SSLProtocol all -SSLv2 -SSLv3
SSLHonorCipherOrder on
SSLCipherSuite ALL:!RC4:!MD5:!ADH:!EXP:!SSLv2:!LOW:!IDEA:RSA:+HIGH:+MEDIUM
<IfModule headers_module>
Header always set Strict-Transport-Security „max-age=29376000“
</IfModule>
SSLCertificateFile /etc/pki/tls/certs/current.crt
SSLCertificateKeyFile /etc/pki/tls/private/current.key
SSLCertificateChainFile /etc/pki/tls/certs/current-ca-chain.pem
<Files ~ „\.(cgi|shtml|phtml|php3?)$“>
SSLOptions +StdEnvVars
</Files>
<Directory „/var/www/cgi-bin“>
SSLOptions +StdEnvVars
</Directory>
SetEnvIf User-Agent „.*MSIE.*“ \
nokeepalive ssl-unclean-shutdown \
downgrade-1.0 force-response-1.0
CustomLog logs/ssl_request_log \
„%t %h %{SSL_PROTOCOL}x %{SSL_CIPHER}x \“%r\“ %b“
</VirtualHost>
Voila, you have an A+ rating at absolutely no cost! – Nice!
If you don’t get an A+ rating, please check the following part at https://www.ssllabs.com